25 Prime Collaboration Tools For Remote Staff Administration Browser Tips, App Integrations, And Productivity
You can set deadlines, add checklists, and even connect recordsdata, multi functional place. Its flexibility allows you to create tailor-made workflows that enhance collaboration and productiveness. You can easily adjust the device to fit various project varieties and team constructions. With Monday.com, you’ll find a way to create versatile project administration workflows tailor-made to your needs. With Asana, you’ll be able to streamline your task management, making collaboration seamless and efficient for distant work. When you need a straightforward method to handle projects visually, Trello shines as a best choice.
Though each software solution for remote groups may help you accomplish that objective, every software is totally different and provides unique features. Take your time to understand your distant team administration needs to ensure you make an informed determination. Software solutions for distant teams are designed to simplify interaction on sure duties. They allow file sharing, real-time communication, and efficient collaboration to contribute to enhancing the quality of the work. Due to geographic separation, distant workforces typically wrestle to take care of fixed and efficient communication. Thankfully, you’ll be able to overcome this challenge using reliable distant group management software program as a communication and collaboration tool.
Avaza excels out there as a end result of its high rankings and positive person feedback. Create discussions at the project stage for basic updates and strategy. It provides you the clarity you should know precisely who’s doing what and when it’s due.
Try a 14-day free trial or sign up for a free plan to explore how SmartSuite might help your group. For instance, you possibly can join customer suggestions information with a research database to draw insights from your customers. Basecamp has a free version that permits you to run one project at a time with 1 GB of cupboard space.
On the opposite hand, companies that couldn’t adapt to post-COVID dynamics or didn’t combine the right remote team instruments had to shut down. A successful remote group setup requires a devoted virtual space for co-workers to deliver collectively their work-related concerns and progress. Leaveboard is a complete leave management system designed to streamline the method of dealing with worker absences. It helps companies effectively track and manage trip days, sick leave, and other types of employee depart, ensuring a smooth workflow and accurate record-keeping. TeamViewer is a comprehensive remote access and remote help software program that allows customers to join to and control computer systems and cell gadgets from wherever. It’s popular for its ease of use and robust options, making it suitable for IT help, distant administration, and on-line conferences.
With these components in thoughts, let’s walk by way of the best tools and apps for distributed teams. Unlike different platforms, RemoteWokr is completely free for distant staff, providing unrestricted entry to a wealth of job alternatives. Moreover, it reassures users that their information is protected, as it neither collects nor sells any database. For groups that want remote work instruments to regularly hop on calls with clients, Dialpad allows you to do that from anywhere with out being tied to call center software or a standard desk cellphone. There are additionally numerous integrations to automatically synchronize your buyer and name information with instruments like Salesforce and Zendesk for a greater, more productive calling expertise.
There are VPN apps for almost all platforms, so even when your worker connects to Wi-Fi in a restaurant from his smartphone, he might be protected. Remote work has steadily gained popularity prior to now decade, due to the emergence of on-line collaboration tools and digitized platforms. Additionally, remote work has been discovered to extend productivity by 13%!
The findings — together with the recommendation shared — from our 2021 Remote Project Management Report makes it a must-read for groups, project managers, and executives. The software ought to join seamlessly with the apps your team already uses, such as your CRM, communication platform, cloud storage, or finance instruments. Smooth integrations forestall duplicate work and maintain info flowing across systems. This means supporting multi-team structures, advanced workflows, larger information sets, stronger automation, admin controls, and enterprise-level governance when needed.
Microsoft OneDrive is a cloud storage service that gives secure access to information from any gadget, with options similar to model control, file sharing, and collaboration. It enables remote staff members to simply retailer, share, and collaborate on documents, ensuring that everyone can access the recordsdata they need, regardless of the place they’re positioned. Wrike is user-friendly and offers a broad vary of features to swimsuit any project, making it a super choice for remote teams trying to enhance their project administration capabilities.
CurrentWare’s worker monitoring instruments supply on-premises knowledge storage with deployment choices that assist the monitoring and managing of remote employees. It could be put in transparently or in stealth mode, with the monitored employee oblivious to the software’s actions. Due to the shortage of a mobile app or cross-platform help, it is best utilized in Windows-based environments. There are plenty of ways to view initiatives in Hubstaff Tasks, including Sprints and Gantt chart views. Whether or not you’ve used a project management tool earlier than, this one is simple to be taught. Managing the intensive documentation required for construction initiatives may be challenging, particularly for distant employees.
Features like task management boards and automatic reminders assist teams operate smoothly and give consideration to priorities. So, instruments with strong encryption, multi-factor authentication, and assembly data protection laws are important. This helps be certain that project information stays protected and trust inside the group stay intact.
It offers a variety of options including task administration, time tracking, useful resource administration, and collaboration instruments. When on the lookout for one of the best project management software program, think about Zenkit. With Zenkit, you’ll get a good unfold of options and templates for simple workspace setup.
Basecamp’s complete set of features makes it a valuable tool for distant teams. In addition to project management, Basecamp provides messaging capabilities that permit group members to communicate successfully. The file storage function ensures that each one project-related documents are easily accessible, promoting collaboration and data sharing. In today’s digital age, remote work has turn into more and more prevalent.
Building a cohesive and productive distant group begins with hiring the best people. Project managers should rigorously choose group members who are self-motivated, unbiased, and possess excellent communication expertise. Additionally, fostering a sense of camaraderie and group spirit via virtual team-building activities helps create a robust bond amongst remote team members.
ClickUp Integrations lets you combine a thousand instruments on a single platform—tools like Dropbox, Slack, Figma, Zoom, Gmail, and more—within your ClickUp Workspace. Team members can share information, hyperlinks, and different information to maintain everybody up to date by way of messages in the Chat View. There are challenges galore, including productivity fluctuations, emotions of isolation and disconnect, communication lapses, and the wrestle to seek out that golden work-life equilibrium. With VirtualSpace, you probably can expertise a digital workspace that brings your team together, regardless of their bodily locations. A important majority of people working remotely roughly 75% recognise the importance of cooperation and collaboration in achieving job success. Time Doctor also provides options like screenshot monitoring and detailed reporting, making it easier to make sure accountability.
With the right skills and techniques, you can transform your strategy to distant work, fostering collaboration and driving results—all from the comfort of your home office. Your staff aren’t mind readers, and when you’re not working collectively in particular person, it might be difficult to know what’s working properly and what wants enchancment. Its consumer interface is clean and intuitive, that includes a sidebar for channels and direct messages, with customizable themes and accessibility options that make navigation straightforward. At the core of all useful retrospectives is a collection of questions aiming to seek out ways to improve the remote collaboration course of. Running a quick retrospective or postmortem after each project cycle is a valuable exception to our rule of avoiding conferences.
To actually unlock their power, you also need the proper setup—because clear communication is every little thing when it comes to working collectively online. Homerun allows you to create posts for vacant roles inside your organization. You can divide your recruitment department into small groups so each can concentrate on a particular hiring objective. We especially like the design of the job posts themselves, which are clean and sleek, making it simple to be taught concerning the role and the finer particulars. If you need more than a kanban board, the Premium plan opens up extra project views within the form of a timeline, table, dashboard or calendar.
While some or all staff members do most or all of their work remotely, remote project management is the discipline of planning and managing a project. In the remote project management model, the project manager can work from home. Using lists and boards, you can pick away at your professional to-do listing and work on a quantity of tasks simultaneously. Learn extra about what the platform offers by reading our Todoist review.
With features like personalized goal-setting and focus tools, RescueTime lets you stay organized and build more effective routines. Helps teams prioritize duties, set deadlines, and stay focused on high-impact tasks. Asana, identical to Trello, lets you create project boards and add sub-tasks so that everyone knows what to do.
TalentDesk is an ideal resolution for helping your distant teammates keep linked whereas dealing with complex projects. The platform empowers distant staff managers and leaders to arrange and handle distributed workforces by way of highly effective productivity and distant group management options. Every distant worker is exclusive, with particular wants, working habits, and so forth. Since they’re working remotely, remote workers can deal with complex projects and duties from totally different places and time zones. This article explores the highest remote work tools that can become your productiveness suite—the apps, communication platforms, and collaboration hubs that can maintain your digital team on track. HeyTaco is likely considered one of the more playful distant staff administration instruments, helping workers really feel related and appreciated.
Jira integrates with developer instruments (GitHub, Bitbucket), CI/CD techniques, Confluence, and lots of third-party apps. Monday.com integrates with Slack, Google Drive, Zoom, Microsoft Teams, and a lot of different instruments, and supports automation actions. Asana is broadly appreciated as a result of it helps both high-level planning and detailed task execution. ClickUp has desktop apps for Windows and Mac, and cellular apps for iOS and Android, permitting full entry whether you’re at your desk or on the go.
With its intuitive interface and customizable channels, Slack helps distant teams stay connected regardless of time zones. As probably the greatest remote staff instruments, Tick comes with a simple time tracker that distant workers can use on a number of platforms — iOS, Android, Apple Watch, PCs, and Macs. Clear communication and regular updates are important for profitable distant project administration. Establish constant channels for communication, corresponding to every day check-ins, weekly staff meetings, and real-time messaging apps like Slack. Regular updates keep everyone on the identical web page and assist shortly address any points or modifications within the project. With ClickUp’s Remote Team options, you get collaboration, productiveness, and project management instruments custom-built for remote work.
However, managing remote groups and projects comes with its unique set of challenges, corresponding to communication limitations, time zone variations, and maintaining group cohesion. Here are some important tips, challenges, and tools that will help you successfully handle remote initiatives. File sharing and cloud storage instruments are vital for remote teams to make sure seamless entry to essential paperwork and collaboration. These tools enable staff to entry files, share documents, and collaborate in actual time, regardless of their bodily location. With the increasing reliance on distant work, a dependable file-sharing solution is crucial for maintaining productiveness and guaranteeing group members can simply collaborate on initiatives. These instruments are essential in guaranteeing streamlined workflow, effective resource allocation, seamless communication, and efficient project execution.
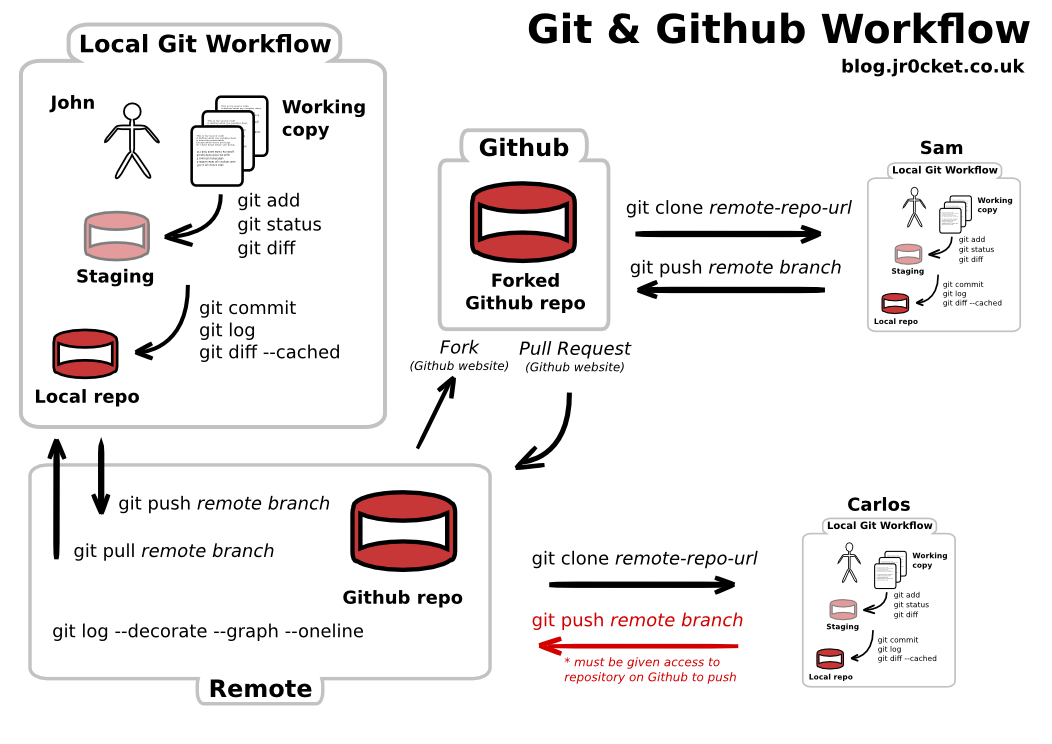
Tmate lets you share your terminal and ssh into another developer’s terminal. I also like to use pull requests to speak what kind of work I’m doing. The intent of a pull request is not to current work that is “finished” and to be added to the code base after a quick code evaluate. Between Miro and Whimsical, not often am I unable to feel like I’m lacking out on collaboration without a whiteboard.
The net interface is easy and intuitive, which makes it easy even for the least tech-savvy users to retailer, access, and share information. The platform removes productiveness bottlenecks by permitting remote teams to share files easily with each other and collaborate on documents, spreadsheets, and presentations. It’s especially a must-have for the remote groups who produce content material or share calendars. When selecting the best device to implement for distant staff management, there are different classes of distant software to contemplate.
These instruments assist streamline processes, enabling group members to collaborate effortlessly regardless of their bodily location. Investing in the proper solutions can significantly improve communication and project monitoring, finally main to raised outcomes. In current years, we have witnessed a significant rise in remote work, driven by technological developments and changing employee expectations. Many organizations have realized that remote work can improve productiveness while offering employees a superb work-life stability.
Harvest can notify them when users are approaching the utmost finances and examine in with their staff to know why projects take longer than anticipated. Managing remote groups can be a challenge, particularly when coordinating day off throughout completely different locations and time zones. That’s why I love Vacation Tracker—it’s user-friendly environment friendly, and fits seamlessly into tools we’re already utilizing, like Slack, Microsoft Teams, and Google Workspace. The Kanban board layout allows teams to visually arrange their duties and monitor progress easily. By moving cards throughout totally different columns, staff members can see the status of each task at a look. Password managers help in ensuring group members use sturdy, completely different passwords per software.
To stay on observe, GreenTech Solutions performed weekly evaluation meetings utilizing Trello’s integrated calendar function. These meetings focused on assessing progress, addressing roadblocks, and realigning duties as needed. Lastly, the platform provides insightful analytics and reporting, serving to useful resource administration groups monitor progress and make data-driven choices to enhance efficiency.
It offers sturdy customization and scalability, making it a strong contender on this listing. While some instruments prioritize simplicity, Wrike excels at adapting to complex workflows. This helps maintain everyone on the identical web page, even across a quantity of departments. A Kanban-style project management software for software program groups utilized by over a thousand companies. This is a popular online project administration and time tracking software program that is widely utilized by distant groups.
Jira is a leading project management device built for software growth groups. While it won’t be the right fit for each distant team, its energy and suppleness make it important for those using Agile and Scrum methodologies. While instruments like Asana and Trello are excellent for pure project management, Notion differentiates itself by integrating project management with documentation and knowledge management. This makes it a powerful all-in-one resolution for distant teams needing extra than simply task administration.
If you’re trying to find a vibrant and fascinating platform to bring your distant staff or event to life, WorkAdventure provides a refreshing and imaginative approach. Gather is an progressive virtual platform that blends video conferencing with customizable, interactive spaces. It permits groups, pals, and occasion organizers to create distinctive environments where customers can transfer round, work together naturally, and collaborate seamlessly. If you’re on the lookout for a inventive and fascinating way to connect remotely, Gather presents a dynamic different to conventional digital assembly instruments.
The emphasis is on environment friendly communication, with each project detail housed within a central space, eradicating the frequent need for status check-ins. By providing instruments to automate recurring duties and providing clear project visibility. Internxt is a “zero knowledge” cloud storage that provides decentralized (encrypted) cloud services. Internxt’s primary product is X Cloud, a cloud storage platform permitting customers to store and share information across a number of gadgets and platforms securely.
Its screenshots, exercise levels, and timesheets provide insights into particular person and team performance, helping managers establish bottlenecks or overworked group members. SmartSuite integrates natively with many instruments, and connects through Zapier or Make to 1000’s more. ClickUp consolidates your tools—but remember the software on your well being. While ClickUp tracks your time and tasks, DeskBreak tracks your wellness. Asana keeps your initiatives organized—DeskBreak retains your staff wholesome. Use DeskBreak’s Asana integration to schedule team breaks between project milestones, making certain productiveness does not come at the worth of wellness.
Through meticulous assessments, I unveil areas ripe for enhancement, orchestrating streamlined workflows and implementing dynamic methods that amplify productiveness across numerous departments. Technology enables managers to handle distant work by optimizing distant work, enhancing team connectedness, and streamlining processes. This transforms an inefficient group into effective staff, bringing a complete new level of engagement. In 2026, technology has taken the highest spot in reinstalling distant IT group management. These trends spotlight the continuing transformation of distant work management.
Many think that team bonding just isn’t attainable if you end up working remotely, that’s not true. Fun on-line actions corresponding to games and trivia or even a informal chat throughout espresso break can make your staff members bond. There’s no single factor performing as a catalyst for more distant working, but quite a combination of technological maturity, worker expectations, and financial pragmatism. Better bandwidth, more sturdy cloud and collaboration platforms, and the teachings learned through the Covid 19 pandemic have made remote work not simply feasible, however often preferable for workers. Playroll is the HR and payroll layer of your remote administration stack – giving finance and people groups the readability they want to do their best work. Some VNC variants assist file transfer, but speeds are gradual and unstable.
The importance of using the best online tools when working remotely cannot be emphasised sufficient. How efficiently the team collaborates is determined by what instruments you utilize and how you employ them. The methodology of managing a project remotely or on-site additionally could differ from firm to company. However, with one of the best practices offered beneath, you can adapt your individual course of to make things more practical. Basically the project administration life cycle consists of 5 stages; project initiation, project planning, project execution, project monitoring, and project closure. We have covered these levels in-depth in our Guide to Understanding the Phases of Project Management Lifecycle.
It’s far more sturdy than simple PM tools like Asana and Trello, but the interface is simple to make use of and could be applied rapidly. It’s full of instruments, templates, and automations that help you retake control of your tasks rather than letting them management you. Countless groups started utilizing it unofficially because it was better than anything at the time. It pulls in collaboration throughout groups (called channels), direct messaging (one-to-one chat), and video calling (with the premium enterprise tier, that is). It’s a super place for remote groups to get fast answers to project questions or notify the next team member in the workflow — without creating difficult e-mail threads.
It contains a customizable digital office house the place your distributed staff can freely navigate and meet colleagues, sparking impromptu discussions and knowledge-sharing. Using Gather, you can even design your personal workstation, have a virtual pet, and roam across the digital office. While the enchantment of flexibility and avoiding day by day commutes is evident, the transition to remote work hasn’t been without its challenges. Successful distant work requires a mindset shift and digital tools to allow communication throughout time zones, collaboration beyond borders, and connection throughout distributed groups.
A solid choice for teams that want structure with out sacrificing ease of use. Asana presents automation, customized fields, dashboards, timeline views, and workflow builders that help teams keep organized. It works nicely for cross-department tasks, particularly if you want visibility into workloads, portfolios, and long-term planning. The device ought to help async updates, offer cell apps, encourage documentation, and make it simple for teams across time zones to stay aligned. This guide lays out the highest platforms, essential options, pricing, and determination factors. It also contains comparisons, mini-reviews, and a look at how Wing Assistant strengthens project administration workflows as a complementary service.

Overall, AirDroid is appropriate for customers who need cross-platform synchronization, distant operation, and wi-fi transfer, making it a relatively mature distant device within the Android ecosystem. You can set customized fields and statuses to match your team’s means of working. The device additionally provides good reminders and reporting to maintain you informed. It supplies a wide range of options, together with display sharing, polling, Q The collaboration features, including file sharing and integrated messaging, promote open strains of communication amongst group members, thereby enhancing problem-solving efficiency.
The project administration software you choose ought to be able to combine with other software program your group is already using. Google Workspace’s cloud-based storage permits for easy access to files from any device, making it excellent for remote groups. It helps real-time collaboration, enabling a number of customers to work on paperwork concurrently. Check Point provides a complete suite of cybersecurity solutions for businesses. Its products offer superior menace prevention, secure distant entry, and knowledge safety. The unified security architecture simplifies management and reduces operational complexity.
The Teramind platform is a user-friendly dashboard with nuanced, real-time information and curated insights to encourage proactive productiveness measures. The software’s advanced analytics capabilities include detailed stakeholder reporting, automated alerts for abnormal exercise, and coverage enforcement to control safe information access precisely. Notta is a gathering productivity software that helps report, transcribe, and summarize video calls on platforms like Google Meet, Microsoft Teams, and Zoom.
This organized method helps create a calmer, more centered work atmosphere for everybody. While Officely isn’t a conventional performance management software, it plays a crucial supporting position in serving to your team meet their objectives. Some software program, like Controlio, provides Key Performance Indicators (KPIs) corresponding to Productivity Score and Active Time to help track efficiency and spot any bottlenecks. When staff members don’t should stress about the place they’ll sit or if a gathering room might be free, they will higher think about their core duties and perform at their best.
AgilityPortal is an all-in-one business-to-business collaboration platform that goes beyond basic task administration. With drag-and-drop functionality and powerful automation instruments, teams can streamline repetitive tasks and customize their workspace to suit any project or industry. Monday.com is a dynamic work operating system that empowers teams to plan, monitor, and manage initiatives with ease.
With a number of project views—like Kanban boards, lists, timelines, and calendars—it caters to various work kinds and project needs. Marketing teams can use Kanban boards for content pipelines, whereas software program development teams might use lists or timelines for sprints. Digital Samba stands out in the distant staff communication tools market with its progressive, browser-based solution. Pioneering in its subject, it provides a REST API and full white labeling capabilities, allowing seamless integration of HD-quality video calls into varied digital purposes.
Remote work tools provide information on employee performance, such as time spent on tasks, productivity levels, and project completion. This helps managers conduct goal and insightful performance critiques. Tools like EmpMonitor guarantee suggestions is predicated on correct knowledge, helping workers establish strengths and areas for enchancment. Remote work instruments are important for making a smooth and environment friendly work surroundings, especially as businesses embrace distributed groups. They enhance communication, streamline workflows, and assist keep productiveness with out micromanagement.
For clarity in workflow management from anywhere, Trello delivers each time. We discovered how important the proper software is for teams working aside. Figma is the web-based interface design device standard, focusing on UI/UX design, prototyping, and design system collaboration, making it glorious for distant design groups. The Trello Free Plan (as of May 1, 2025) helps as a lot as 10 collaborators per Workspace and allows for 10 boards per Workspace. While storage is technically unlimited, there’s a 10MB per file restrict.
This readability not only helps in keeping projects on observe but also fosters accountability amongst staff members. As a nicely known collaboration tool for distant groups, Asana helps groups stay organized with their duties. It enables teams to plan and manage their work in a centralized platform.
This unified communication ecosystem can present distant staff leaders with insights into the progress and challenges of their groups. Brosix is an prompt messaging platform designed to assist groups talk more easily. Brosix offers its shoppers a non-public group network, which provides an unique and secure collaboration house. Its software permits groups to work collectively more successfully and share real-time data. Brosix file transfers and screen-sharing features can help distant software improvement groups stay related.
Many instruments supply tiered pricing, allowing you to begin with a lower-cost plan and scale up as your needs develop. It’s important to weigh the tool’s value in opposition to its potential to enhance productivity and efficiency. Empuls is an all-in-one employee engagement platform designed to foster connection, collaboration, and motivation within groups. If you’re in search of a holistic resolution to reinforce engagement and productivity, Empuls is a powerful selection. Since these are automated, you only have to set them up as quickly as, and it’ll continue to reward staff primarily based on their efficiency.
We’ll resolve any uncertainty you would possibly have and help you resolve which software is one of the best for you and your staff of remote employees. Effective danger administration is essential in remote project administration, starting with the identification of potential dangers. Early identification permits groups to proactively tackle issues before they escalate into vital roadblocks. Conducting a thorough threat assessment at the distant project manager’s outset is crucial. This involves evaluating all elements of the project, from useful resource availability to potential technological challenges. Creating a collaborative culture inside remote groups requires an surroundings the place open communication and mutual support are encouraged.
Then, grab a pen, and let’s observe the most effective instruments to make use of in your software program improvement project. As you presumably can see from this list, there’s a distant working tool for pretty much every little thing you are in a position to do in an office. Be it engaging with fellow staff, speaking with them, recognizing their good work, or holding conferences, there’s a software that facilitates each office activity. For groups working throughout completely different time zones, aligning schedules for real-time collaboration can be difficult, resulting in delays and frustration. Investing in a considerate home office setup isn’t just about comfort—it’s about sustaining efficiency. The proper equipment can flip your home into a productive, professional workspace.
Engage your remote team in this endeavor; their frontline experience can present invaluable insights. While mapping out tool specs, segregate them into indispensable features and those who could be good additions. The platform additionally provides a variety of different features, including the power to set up a quantity of clocks for different time zones and to view time zone maps and daylight saving time info.
Cloud-based storage techniques are great remote management instruments for file sharing. Unlike in-house file storage systems which might be only accessible regionally, recordsdata on the cloud are accessible to staff members at any time no matter their geographical location. When it involves people, they allow you to onboard expertise in different time zones, run payroll in multiple currencies, handle advantages, and guarantee compliance with native laws. The platform is structured around workspaces that contain tasks, and within those initiatives, duties can be organized into packages for higher organization.
People are busy, and this assembly will not be the only task in your team’s calendars for the day. Just like in-person conferences have a set time restrict, ensure your virtual conferences do as properly. If group members need to discuss things that are not on the agenda, let them know that you will notice them, and so they’ll be handled on the subsequent catch-up. A project planning tool like Float allows you to tentatively assign duties to team members or create tasks and mark them as unassigned to return to later. With the best remote team instruments in your belt, you’ll find a way to efficiently monitor and motivate your remote workers.
Instead of counting on lagging indicators or holding more meetings, predictive approaches constantly combine stakeholder suggestions and proven patterns to determine early-warning alerts. They spotlight the place sentiment is drifting, the place selections are stalling, and the place necessities are unstable, typically weeks ahead of visible slippage. Encouraging open, transparent communication is crucial in stopping misunderstandings.
With a distant model, there’s merely no approach to succeed without providing clear reporting. As a end result, project managers managing remote groups rely even more heavily on tracking and feedback than traditional PMs. With the proper techniques in place, staff and leaders alike can have a clearer, extra transparent image of how issues are going. Over time, individuals really feel disconnected, which erodes high quality and timelines. Adopting the proper project management software program makes managing distant tasks extra efficient and efficient, ensuring project success. Clear and concise communication is essential in remote project management.
It runs quietly within the background in your laptop and telephone, mechanically monitoring the time you spend on totally different applications and web sites. This gives you a clear, private image of your digital habits, helping you perceive where your time really goes and determine your greatest distractions. It’s incredible for anyone seeking to build higher focus and reclaim their time. In a hybrid setting, encouraging staff members to make use of such a software can foster a tradition of aware work and self-awareness.
Encourage open communication so your team feels comfy sharing thoughts and asking questions. By offering constructive feedback frequently, you assist your team make necessary adjustments and keep centered on delivering nice outcomes. Use project management instruments to assign duties and keep every thing organized. These platforms make it easy for every staff member to see their responsibilities, observe deadlines, and perceive how their work matches into the bigger image. It helps everyone keep aligned and ensures nothing falls through the cracks. Once you’ve assigned the duties, take a moment to confirm that everyone absolutely understands their position.
It’s simple to use a Kanban board, even when you’ve never used a structured project administration type earlier than. When a team member begins working on a task, they move it from the To-Do column to the Doing column. The building trade has historically been hands-on, requiring on-site presence to manage workers, examine progress, and guarantee deadlines are met. However, with the fast evolution of technology, project administration in development has taken on a model new type.
It permits you to create advanced dashboards with features, and it additionally enables you to visualize your resources. And with ClickUp’s AI-powered Calendar, you get smart ideas to schedule duties at the proper time primarily based on precedence, availability, and workload—keeping everybody aligned without the guesswork. If you’re nonetheless juggling a number of instruments, or questioning if there’s a more highly effective centralized choice, ClickUp is value a severe look. A typical day within the life of a project manager is a continuing whirlwind of racing after deadlines, juggling sources, and interesting stakeholders—each of these is an uphill climb. Focus on making a system that assesses productivity utilizing the metrics listed above as a substitute of tracking work time. Different states and countries additionally require companies to be compliant with tax and employment laws.
While newer and fewer proven than alternate options, Height’s autonomous options scale back PM busywork, letting groups concentrate on precise work quite than organizing duties. Todoist is primarily a personal task manager that also works for small teams. Its simplicity—just duties, initiatives, and labels—makes it good for people or small groups that do not want full project management features. Todoist’s pure language input (‘tomorrow at 3pm’) and keyboard shortcuts make task capture effortless. While missing superior PM features, its simplicity and affordability are its strength. Teamwork excels in client administration, with invoicing and consumer entry options that streamline exterior collaboration.